Wordpress Malware Ecosystem 1
Something upwards of 40% of all Internet websites use WordPress blogging software. WordPress is written in the PHP programming language. Because PHP has a lot of quirks, and because just about any wanker can come along and crap out a solution to any given problem, WordPress installations have traditionally had security flaws. That makes WordPress installations subject to a lot of shady activity.
There are sub-industries devoted to activities like brute-force-guessing admin passwords of WordPress sites, and then selling that illicit access There are apparently people who do feral software engineering, mostly in PHP, to support financial exploitation of cracked WordPress blog installations.
I ran an Apache HTTP server out of my basement for years.
I read the access_log files to see what people looked at.
Over the years I noticed an increasing number of puzzling accesses.
I started to write HTML and/or CGI-BIN programs that captured POST
parameters and other information about those puzzling accesses.
Ultimately, I wrote a fake WordPress website,
a “low interaction” honey pot.
I ran it for a few years, roughly from 2013 to 2018.
I wrote up the initial run,
which went from May to September of 2013.
I ended up re-writing my first fake WordPress installation, and running it for 3 or 4 more years. I had to update more-or-less continuously to keep up with what the Internet Bottom Feeders throw at WordPress. I caught a great deal of WordPress and PHP malware. It roughly fits into categories like this:
- Email spamming tools
- Access verification
- Reconnaisance
- Web shells
- Backdoors
- SOCKS servers
- HTTP redirectors
- File Managers
- Password guessers
Web shells in particular interest me. If they were installed deliberately, they’d mostly qualify as poorly-coded remote administration tools, like Dameware on Windows. They’re very popular, they get downloaded to cracked WordPress sites all the time.
There were a large variety of web shells in common use while I ran my fake WordPress. The most common web shell that got caught by my fake WordPress is Web Shell by oRb or “WSO”, also known as “FilesMan”.
WSO derives from a real development cycle by someone (“oRb”). It has versions, bug fixes, added features, and even presumably unused or unreliable code that got removed. Some effort went into concealing installed WSO files from search engines.
At one point some Russian-language people hosted a separate development effort on github.com. There’s a real evolution of WSO over time.
It has also been the object of large amounts of feral software engineering. Lots of Evil Hackers have changed it here and there for whatever reasons, adding specific functions, showing a different banner.
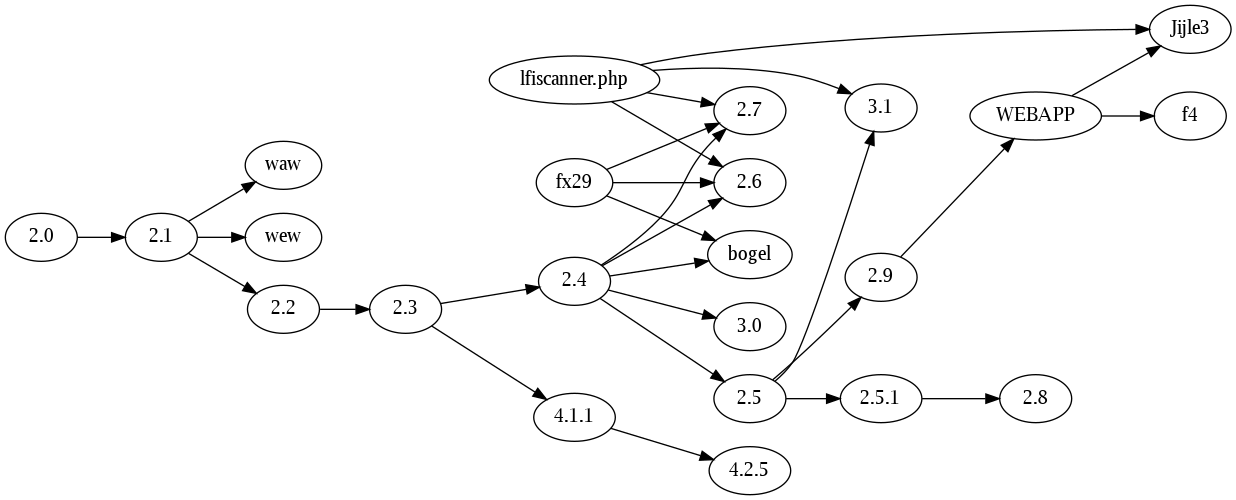
WSO provides a case study in feral software engineering.
In-the-wild use of web shells puzzles me.
As near as I can tell, hardly anybody uses them interactively.
WSO actually has a “backdoor” like method, actionRC,
that is used to run PHP code on a cracked WordPress site without interactivity.
actionRC gets invoked a lot more often than anything used by Real Humans.
This seems paradoxical given the amount of effort that Evil Hackers
put into customizing and extending WSO for their own Evil Purposes.
